LAN Fundamentals
* straight trough, crossover
* RJ-45 male connector:
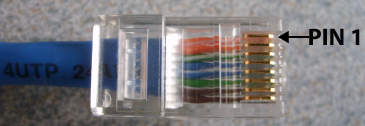
* Pin layouts for straight-through, crossover and rollover cables:
* Use a rollover cable when connecting to the console port of a switch or router.
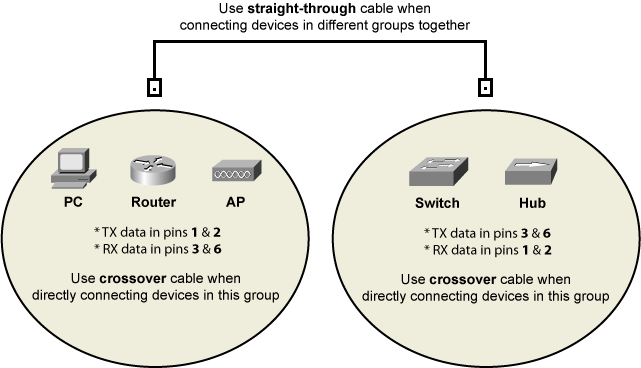
* Use crossover cables when making connections among devices in the same group. Use straight-through cable when connecting devices in the opposite group:
* Gigabit Ethernet:
802.3ab.- 1000BASE-T
802.3z.- 1000BASE over fiber optic
* Ethernet modes that support distances greater than 550 meters
1000BASE-LX
1000BASE-ZX
* mac address 48 bits. First 24 bits: OUI.
Routers & Switches
*
* Common configuration registers:
* SYST LED switch solid amber, POST failed, cisco ios did not load and system is malfunctioning.
* switch port flashing green/amber: port is expiriencing errors.
* Console port settings:
* rollover cable for console connections
*
* setting console password
* copy running-config startup-config
* enable secret and enable password for privileged mode
* logging synchrounous and exec-timeout commands
* service password-encryption
* configuring switch IP address
* switch default gateway
* telnet and ssh configuration
* Creating a connection to a remote switch or router using Telnet:
* Terminate a session in the remote router or switch:
*
* CDP
* Use the following command to enable/disable CDP for the entire switch or router:
-store and forward.- The switch receives the complete frame before beginning to forward it. Latancy through the swtich varies with frame lenght. Filters all errors and latancy increases.
Wireless LANs
* WLAN modes:
* WLAN security standards:
* WEP and TKIP security protocols are based on the RC4 encryption algorithm.
* WPAv1 is preferred over WEP because WPAv1 key values can change dynamically while the system is used.
* Overlap ESS cells coverage by at least 10% to prevent users to lose connectivity.
* WPA2 = 802.1i
* Rogue AP = unauthorized access point.
VLANs
* Adding a VLAN:
normal range 1-1001
extended range 1006-4095 (only transparent mode)
vlans 1002-1005 are automatically created and cannot be deleted.
* Specifying a maximum number of mac addresses (command defaults to 1):
* Miscellaneous VLAN commands:
* 802.1q trunking protocol:
VTP
* VLAN Trunking Protocol. VTP simplifies switch administration by allowing switches to automactically share VLAN configuration information.
* VTP helps to limit configuration errors by keeping VLAN naming consistent accross the VTP domain.
* Maintans VLAN consistency across a switched network.
* VTP advertisements are delivered to to switches as multicast frames.
* Each time a server modifies its VLAN configuration, the VTP server increments the database revision number by 1. When another client or server receives a VTP message with a higher configuration number thatn its own, the switch updates its VLAN configuration.
* 3 requirements for VTP to working among switches:
* VLAN configuration can be added only in a server, all other servers and clients will learn the new configuration.
* Clients can not be used to configure VLAN information.
* Transparent mode ignores VTP, but forwards VTP messages.
* VTP prunning. Increases available bandwidth in trunk links. Allows to dynamically determine which switches do not need frames from certain VLANs, the VTP prunes those VLANs from the appropriate trunks. This is equivalent to manually set an allowed VLAN list.
* VTP miscellaneous commands:
*Spanning Tree Protocol. Prevents frame loops in redundant switch configurations.
* Bridge ID = priority + MAC
* Priority = 32768 + VLAN ID , so for VLAN 1 the priority is 32769.
* The switch with the lowest bridge id becomes the root bridge (if priorites tie in the bridge id, the lowest MAC wins).
* All ports in the root bridge become designated ports, thus their port state is forwarding.
* Non-root switches must select a root port, this is the port that receives the lowest cost to reach the root bridge. The root port state is forwarding.
* All other LAN segments (connections between non-root switches) must select a designated port. Selection criteria:
* Port Costs (defaults):
* PortFast enhances the STP (802.1d) convergence time on ports that are connected to hosts. When port fast is on, as soon as the the NIC is active, the switch port can move to a forwarding state. Listening and learning states are skipped. Cisco proprietary.
* Enabling PortFast:
* Enabling BPDU Guard:
*Port Roles:
-STP (802.1D)
* Cisco switches use 802.1d with PVST+ by default.
* PVST+ is a Cisco proprietary feature that creates an instance of STP (802.1d) for each VLAN. It allows the root switch location to be optimized per VLAN.
* RPVST (also called PVRST) is a cisco proprietary features that creates an instance of RSTP (802.1w) for each VLAN.
* RPVST stands for Rapid Per VLAN Spanning Tree.
* PVRST stands for Per VLAN Rapid Spanning Tree.
* MIST (802.1s) is a IEEE standard feature that creates an instace of RSTP (802.1w) for each VLAN. Also called MST.
* Comparing STP modes:
*STP configuration commands:
* Subnetting table (download):

* Given 172.168.5.46/29. Find the network number, number of assignable IPs and host range using the table:
* Given 172.168.5.157/27. Find the network number, number of assignable IPs and host range using the table:
* Given 172.168.5.25/28. Find the network number, number of assignable IPs and host range using the table:
* Given 192.168.10.231/27. Find the network number, number of assignable IPs and host range using the table:
* Given 172.168.97.91/18. Find the network number, number of assignable IPs and host range using the table:
* Given 10.29.45.6/21. Find the network number, number of assignable IPs and host range using the table:
* Given 10.9.68.14/15. Find the network number, number of assignable IPs and host range using the table:
Remember the network range is from 172.168.64.0 to 172.168.127.255, but we do not use the first and last addresses.
* Cisco routers will reject configuration of networks that overlap with already configured networks in local interfaces.
* ip subnet zero
ACLs
* ACL ranges:
* Standard ACL example:
* Specify more specific rules first, deny or allow TCP/UDP/ICMP rules first.
* IP Named ACLs.- Allow the deletion of a single statement in the list, allows naming of the list; Can be standard or extended.
* IP Named ACLs examples:
* Dynamic ACLs (Lock & Key).- The router asks for a username and password; after successfully authenticating the user, the router dynamically changes its ACL to permit traffic from the IP address of the host that just sent the authentication packet. After a period of time, the router removes the dynamic entry in the ACL.
* Reflexive ACLs.- An enterprise user must first initiate a new session, then the router records the source and destination IPs and ports, as a result the reflexive ACL will only allow packets whose addresses and ports matches the original packet.
* Time Based ACLs.-
IP Routing
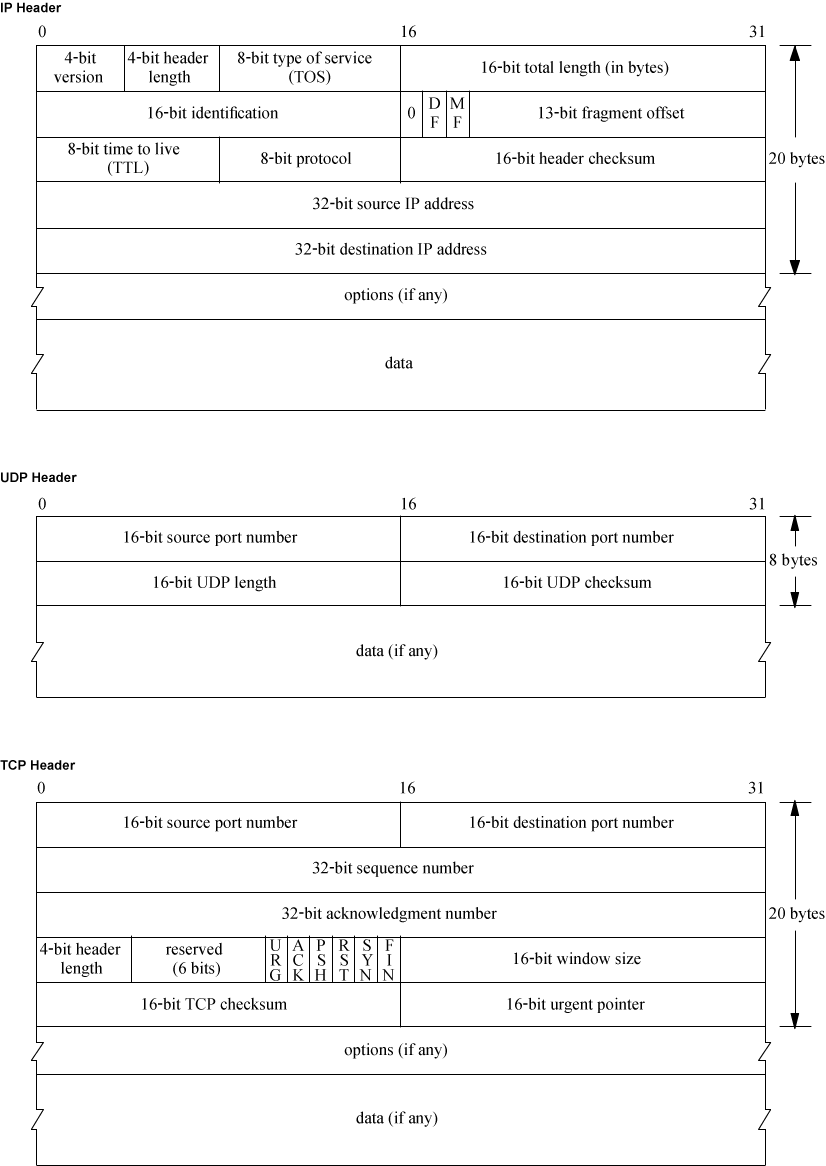
* IP, TCP and UDP headers:
* Common protocols that use TCP/UDP:
* Flow control mechanisms provide receiving hosts a way to control the transmission speed. Flow control mechanisms include : congestion avoidance, windowing, buffering.
* Classful and Classless routing dictate how a default route is used:
* Autosumarization and manual sumarization
* PING
* Extended PING features:
* TRECEROUTE
* TTL expired in transit: routing loop
* IP routing protocols (Interior Routing Protocols):
* Use the nework command to turn routing interfaces
RIP
Timers (in seconds)
Update: 30
Invalid: 180
Hold Down: 180
Flush: 240
OSPF
* Router ID selection proccess
• The router sending the Hello with the highest OSPF priority setting becomes the DR.
• If two or more routers tie with the highest OSPF priority setting, the router sending the Hello with the highest RID wins.
• It's not always the case, but typically the router with the second-highest OSPF priority becomes the BDR.
• An OSPF priority setting of 0 means that the router does not participate in the election and can never become the DR or BDR.
• The range of OSPF priority values that allow a router to be a candidate are 1 through 255.
• If a new, better candidate comes along after the DR and BDR have been elected, the new candidate does not preempt the existing DR and BDR.
EIGRP
* Differentiates between internal and external routes.
* Uses a 32-bit metric.
WANs
* HDLC
* PPP link username and password
(config-if)# ppp authentication chap pap
* Frame-Relay PVC encapsulations:
* Frame Relay LMI types:
NAT
* Static NAT configuration:
* IPsec.- Open standard framework that is commonly used in VPNs to provide secure end-to-end connections
* Data Integrity.- Ensures that data is unaltered between the sender and the recipient.
* Data integrity algorithms: HMAC-MD5 and HMAC-SHA-1
* Authentication.- Ensures that data can be read only by its intented recipent.
* ESP.- Provides confidentiality.
IPv6
* EUI-64 address format
* Multicast address for all routers in the same network segment: FF02::2
Debug Commands
* debug PPP authentication
* straight trough, crossover
* RJ-45 male connector:

* Pin layouts for straight-through, crossover and rollover cables:
|
|
|
||||||||||||||||||||||||||||||||||||||||||||
* Use a rollover cable when connecting to the console port of a switch or router.
* Use crossover cables when making connections among devices in the same group. Use straight-through cable when connecting devices in the opposite group:

* Gigabit Ethernet:
802.3ab.- 1000BASE-T
802.3z.- 1000BASE over fiber optic
* Ethernet modes that support distances greater than 550 meters
1000BASE-LX
1000BASE-ZX
* mac address 48 bits. First 24 bits: OUI.
Routers & Switches
*
* Common configuration registers:
- 0x2102.- Default
- 0x2142.- Skips any startup-config store in NVRAM
* SYST LED switch solid amber, POST failed, cisco ios did not load and system is malfunctioning.
* switch port flashing green/amber: port is expiriencing errors.
* Console port settings:
- Baud rate (bps): 9600
- Data: 8 bit
- Parity: none
- Stop: 1 bit
- Flow control: none
* rollover cable for console connections
*
* setting console password
* copy running-config startup-config
Action |
Command |
New Command |
|---|---|---|
| Copy running configuration to NVRAM | R1# copy running-config startup-config |
R#1 copy system:running-config nvram:startup-config |
| Copy running configuration to NVRAM | R1# write memory |
R#1 copy system:running-config nvram:startup-config |
| Erase configuration in NVRAM | R1# erase startup-config |
R1# erase nvram: |
| Erase configuration in NVRAM | R1# write erase |
R1# erase nvram: |
| Copy running configuration to TFTP | R1# copy running-config tftp |
R1# copy system:running-config tftp:running-config |
| Copy startup configuration from TFTP | R1# copy tftp startup-config |
R1# copy tftp:startup-config nvram:startup-config |
| Lists the file system in platform | R1# show file systems |
|
* enable secret and enable password for privileged mode
* logging synchrounous and exec-timeout commands
* service password-encryption
* configuring switch IP address
* switch default gateway
* telnet and ssh configuration
* Creating a connection to a remote switch or router using Telnet:
R1#telnet 10.75.65.148* Creating a connection to a remote switch or router using SSH:
R1#ssh 10.85.95.105* Telnet & SSH session management:
R1#show sessions /* alias: R1# where */
R1#disconnect 1
R1#resume 2
* Suspend command: ctrl-shift-6 and then x ; It suspends a ssh or telnet session and returns user to client router or switch.* Terminate a session in the remote router or switch:
R5#exit
R1#
* terminal monitor command *
* CDP
* Use the following command to enable/disable CDP for the entire switch or router:
R1(config)# cdp run
* To enable/disable CDP per interface issue:
R1(config-if)# cdp enable
* switching flavors-store and forward.- The switch receives the complete frame before beginning to forward it. Latancy through the swtich varies with frame lenght. Filters all errors and latancy increases.
Wireless LANs
* WLAN modes:
- Ad-hoc
- IBSS (Independent Basic Service Set).- Direct communication between devices. No AP needed.
- Infrastucture mode
- BSS (Basic Service Set).- A WLAN deployment with only 1 AP.
- ESS (Extended Service Set).- A WLAN deployment with 2 or more APs.
Modulation |
Frequency |
Standard Speeds (Mbps) |
|
|---|---|---|---|
| 802.11b | DSSS |
2.4 GHz |
1, 2, 5.5, 11 |
| 802.11g | DSSS/OFDM |
2.4 GHz |
6, 12, 24 |
| 802.11a | OFDM |
5 GHz |
6, 12, 24 |
* WLAN security standards:
Encryption |
Key Distribution |
User Authentication |
Device Authentication |
|
|---|---|---|---|---|
| WEP | RC4 |
Static |
No |
Yes (weak) |
| WPA | TKIP (RC4) |
Static/Dynamic |
Yes |
Yes |
| WPA2 | AES-CCMP |
Static/Dynamic |
Yes |
Yes |
* WEP and TKIP security protocols are based on the RC4 encryption algorithm.
* WPAv1 is preferred over WEP because WPAv1 key values can change dynamically while the system is used.
* Overlap ESS cells coverage by at least 10% to prevent users to lose connectivity.
* WPA2 = 802.1i
* Rogue AP = unauthorized access point.
VLANs
* Adding a VLAN:
SW1(config)#vlan "vlan-id"
SW1(config-vlan)#name "vlan-name"
* Adding an interface to a VLAN:
SW1(config-if)#switchport access vlan "vlan-id"
* Adding an IP phone (a trunk is used from switch to phone):
SW1(config-if)#switchport voice vlan "vlan-id"
* VLAN rangenormal range 1-1001
extended range 1006-4095 (only transparent mode)
vlans 1002-1005 are automatically created and cannot be deleted.
* Specifying a maximum number of mac addresses (command defaults to 1):
SW1(config-if)#switchport port-security maximum "number"
* Specifying a static mac address (use multiple times to indicate more than 1 entry):
SW1(config-if)#switchport port-security mac-address "mac"
* Dynamically learn a mac address:
SW1(config-if)#switchport port-security mac-address sticky
* Specify port-security mac violation mode (default is shutdown):
SW1(config-if)#switchport port-security violation [protect | restrict | shutdown]
| Protect | Restrict | Shutdown | |
|---|---|---|---|
| Discards offending Traffic: |
Yes |
Yes |
Yes |
| Sends logs and SNMP messages: |
No |
Yes |
Yes |
| Disables the interface, discards all traffic: |
No |
No |
Yes |
* Miscellaneous VLAN commands:
SW1(config)#shutdown vlan "vlan-id"
SW1(config)#no shutdown vlan "vlan-id"
SW1(config)#no vlan "vlain-id"
SW1#delete vlan.dat
SW1(config-if)#switchport trunk allowed vlan [add | all | remove | except "vlan-list"]
* Disabling trunk negotiation:
SW1(config-if)#switchport nonegotiate
SW1(config-if)#switchport mode access
* Switch port modes:
SW1(config-if)#switchport mode [access | trunk | dynamic desirable | dynamic auto]
- access .- End users.
- trunk.- Manually (static) specifying port is trunk.
- dynamic desirable.- Initiates trunk negotiation.
- dynamic auto.- just waits (default).
* 2 dynamic auto do not form a trunk.
* Router trunk configuration:
R1(config-subif)#encapsulation dot1q "vlan-id"
* Selecting a VLAN as native:
R1(config-subif)#encapsulation dot1q "vlan-id" native
* Selecting trunk encapsulation (recent Cisco switches do not support isl):
SW1(config-if)#switchport trunk encapsulation isl
* Miscellaneous switch management commands:
SW1#show interfaces status
SW1#show interfaces switchport
SW1#show interfaces trunk
SW1#show ip interfaces brief
SW1#show interfaces fa0/1 status
SW1#show interfaces fa0/1 switchport
SW1#show interfaces fa0/1 trunk
SW1#show mac-address-table
SW1#show mac-address-table dynamic address "mac"
SW1#show vlan
SW1#show etherchannel 1 summary
SW1#show port-security interface f0/13
* ISL trunking protocol.- Encapsulates a normal ethernet frame before forwarding it over a trunk. Cisco propriatery.* 802.1q trunking protocol:
- Does not encapsulate a normal ethernet frame before forwarding it, instead inserts a header after the destination and source mac address.
- Uses a concept of a native VLAN. No tag.
- Supported by IP phones and 2960 switches.
- Multiple physical links treated as one trunk.
- Increaseas network bandwidth.
- Up to 8 physical links (same speed).
- Load balance.
SW1(config-if)#channel-group 1 mode onVTP
* VLAN Trunking Protocol. VTP simplifies switch administration by allowing switches to automactically share VLAN configuration information.
* VTP helps to limit configuration errors by keeping VLAN naming consistent accross the VTP domain.
* Maintans VLAN consistency across a switched network.
* VTP advertisements are delivered to to switches as multicast frames.
* Each time a server modifies its VLAN configuration, the VTP server increments the database revision number by 1. When another client or server receives a VTP message with a higher configuration number thatn its own, the switch updates its VLAN configuration.
* 3 requirements for VTP to working among switches:
- The link between switches must be a trunk.
- VTP domain name must match (case sensitive).
- If set, passwords must match (case sensitive).
- Global configuration mode:
SW1(config)#vtp version 2 SW1(config)#vtp mode [server | client | transparent] SW1(config)#vtp domain "domain_name" SW1(config)#vtp password "password" SW1(config)#vtp pruning - VLAN database mode:
SW1(vlan)#vtp client|
* VLAN configuration can be added only in a server, all other servers and clients will learn the new configuration.
* Clients can not be used to configure VLAN information.
* Transparent mode ignores VTP, but forwards VTP messages.
* VTP prunning. Increases available bandwidth in trunk links. Allows to dynamically determine which switches do not need frames from certain VLANs, the VTP prunes those VLANs from the appropriate trunks. This is equivalent to manually set an allowed VLAN list.
* VTP miscellaneous commands:
SW1#show vtp status
SW1#show vtp password
STP*Spanning Tree Protocol. Prevents frame loops in redundant switch configurations.
* Bridge ID = priority + MAC
* Priority = 32768 + VLAN ID , so for VLAN 1 the priority is 32769.
* The switch with the lowest bridge id becomes the root bridge (if priorites tie in the bridge id, the lowest MAC wins).
* All ports in the root bridge become designated ports, thus their port state is forwarding.
* Non-root switches must select a root port, this is the port that receives the lowest cost to reach the root bridge. The root port state is forwarding.
* All other LAN segments (connections between non-root switches) must select a designated port. Selection criteria:
- The end of the segment that advertises the lowest path cost to the root become the designated port.
- If both ends advertise the same cost to the root, the port in the switch with the lowest BID (priority+mac) wins.
- If costs and mac addresses are the same ( occur in connections to the same switch), lowest remote port priority.
- Finally if everything ties, the lowest remote port id (port number) wins.
* Port Costs (defaults):
| Port Speed | STP Cost |
|---|---|
|
10 Mbs |
100 |
100 Mbs |
19 |
1 Gbs |
4 |
10 Gbs |
2 |
* PortFast enhances the STP (802.1d) convergence time on ports that are connected to hosts. When port fast is on, as soon as the the NIC is active, the switch port can move to a forwarding state. Listening and learning states are skipped. Cisco proprietary.
* Enabling PortFast:
SW1(config-if)#spanning-tree portfast
* BPDU Guard is a feature that automatically disables the port in an operational PortFast upon receipt of a BPDU. Cisco proprietary.* Enabling BPDU Guard:
SW1(config-if)#spanning-tree bpdu guard
* Port States:| STP (802.1D) Port State | RSTP (802.1w) Port State | Is Port Included in Active Topology? | Is Port Learning MAC Addresses? |
|---|---|---|---|
| Disabled | Discarding | No | No |
| Blocking | Discarding | No | No |
| Listening | Discarding | Yes | No |
| Learning | Learning | Yes | Yes |
| Forwarding | Forwarding | Yes | Yes |
*Port Roles:
-STP (802.1D)
- Root Port (Port State: Forwarding)
- Designated Port (Port State: Forwarding)
- Root Port (Port State: Forwarding)
- Designated Port (Port State: Forwarding)
- Alternate Port
- Backup Port
* RSTP expands the STP port roles by adding the alternate and backup roles. RSTP defines new port roles.
* RSTP is compatible with the original STP (802.1d).
* RSTP significanlty reduces topology reconverging time after a link failure.
* RSTP
provides a faster transition to the forwarding state on point-to-point than STP does.
* STP with PortFast= RSTP/Link-Type Edge.
* RSTP does not do anything different thank STP on Link-Type Shared.
* RSTP is better in Link-Type Point-to-Point.
* Command to enable RSTP in a Cisco Switch:
SW1(config)#spanning-tree mode rapid-pvst
* RSTP (802.1w) and STP (802.1d) do not natively support multiple instances of STP.* Cisco switches use 802.1d with PVST+ by default.
* PVST+ is a Cisco proprietary feature that creates an instance of STP (802.1d) for each VLAN. It allows the root switch location to be optimized per VLAN.
* RPVST (also called PVRST) is a cisco proprietary features that creates an instance of RSTP (802.1w) for each VLAN.
* RPVST stands for Rapid Per VLAN Spanning Tree.
* PVRST stands for Per VLAN Rapid Spanning Tree.
* MIST (802.1s) is a IEEE standard feature that creates an instace of RSTP (802.1w) for each VLAN. Also called MST.
* Comparing STP modes:
| Mode | STP (802.1d) Support | RSTP (802.1w) Support |
|---|---|---|
|
PVST+ |
Yes |
No |
RPVST |
No |
Yes |
MIST |
No |
Yes |
*STP configuration commands:
SW1#show spanning-tree
SW1#show spanning-tree root
SW1#show spanning-tree bridge
SW1#show spanning-tree interface fa0/1
SW1(config)#spanning-tree mode [rapid-pvst | pvst | mst]
SW1(config)#spanning-tree vlan 1 priority "0-61440"
SW1(config)#spanning-tree vlan 1 root primary
SW1(config)#spanning-tree vlan 1 root secondary
SW1(config-if)#spanning-tree cost "1-200,000,000"
SW1(config-if)#spanning-tree vlan "vland_id" cost "1-200,000,000"
VLSM* Subnetting table (download):

* Given 172.168.5.46/29. Find the network number, number of assignable IPs and host range using the table:
- /29 corresponds to 248 and indicates that VLSM is applied in the fourth octet of the subnetmask and the IP address. So the decimal subment mask is 255.255.255.248 .
- Find the network increment: 256-248=8, the network increment is 8 .
- Starting from 0 write all networks until passing the fourth octect (.46) of the given IP address (increments of 8): 0, 8,16, 24, 32, 40, 48 ...
- We now know the given IP (fourth octect) is in between ...40 and 48... networks, we always choose the lowest one, in this case 40. That is the network number, 172.168.5.40!
- Finding the number of assignable IPs is easy. From step b): 8-2=6, we can assign 6 IPs (the network can support 6 hosts), we needed to subtract 2 from the network increment because there are two address that cannot be assigned to hosts, the broadcast address (.47 , last IP) and the network address itself (.40).
- The first assignable IP is always one more than the network number, so the first valid IP address is 172.168.5.41 .
- The last assignable IP is always one less than the broadcast address, so the last valid IP address is 172.168.5.46 .
* Given 172.168.5.157/27. Find the network number, number of assignable IPs and host range using the table:
- /27 corresponds to 224 and indicates that VLSM is applied in the fourth octet of the subnetmask and the IP address. So the decimal subment mask is 255.255.255.224 .
- Find the network increment: 256-224=32, the network increment is 32 .
- Starting from 0 write all networks until passing the fourth octect (.157) of the given IP address (increments of 32): 0, 32, 64, 96, 128, 160 ...
- We now know the given IP (fourth octect of the IP) is in between ...128 and 160... networks, we always choose the lowest one, in this case 128. That is the network number, 172.168.5.128!
- Finding the number of assignable IPs is easy. From step b): 32-2=30, we can assign 30 IPs (the network can support 30 hosts), we needed to subtract 2 from the network increment because there are two address that cannot be assigned to hosts, the broadcast address (.159 , last IP) and the network address itself (.128).
- The first assignable IP is always one more than the network number, so the first valid IP address is 172.168.5.129 .
- The last assignable IP is always one less than the broadcast address, so the last valid IP address is 172.168.5.158 .
* Given 172.168.5.25/28. Find the network number, number of assignable IPs and host range using the table:
- /28 corresponds to 240 and indicates that VLSM is applied in the fourth octet of the subnetmask and the IP address. So the decimal subment mask is 255.255.255.240 .
- Find the network increment: 256-240=16, the network increment is 16 .
- Starting from 0 write all networks until passing the fourth octect (.25) of the given IP address (increments of 16): 0, 16, 32, 48, 64, 80 ...
- We now know the given IP (fourth octect of the IP) is in between ...16 and 32... networks, we always choose the lowest one, in this case 16. That is the network number, 172.168.5.16!
- Finding the number of assignable IPs is easy. From step b): 16-2=14, we can assign 14 IPs (the network can support 14 hosts), we needed to subtract 2 from the network increment because there are two address that cannot be assigned to hosts, the broadcast address (.31 , last IP) and the network address itself (.16).
- The first assignable IP is always one more than the network number, so the first valid IP address is 172.168.5.17 .
- The last assignable IP is always one less than the broadcast address, so the last valid IP address is 172.168.5.30 .
* Given 192.168.10.231/27. Find the network number, number of assignable IPs and host range using the table:
- /27 corresponds to 224 and indicates that VLSM is applied in the fourth octet of the subnetmask and the IP address. So the decimal subment mask is 255.255.255.224 .
- Find the network increment: 256-224=32, the network increment is 32 .
- Starting from 0 write all networks until passing the fourth octect (.231) of the given IP address (incremets of 32): 0, 32, 64, 96, 128, 160, 196, 224, 256 (we always stop when we get to 256).
- We now know the given IP (fourth octect of the IP) is in between ...224 and 256... networks, we always choose the lowest one, in this case 224. That is the network number, 192.168.10.224!
- Finding the number of assignable IPs is easy. From step b): 32-2=30, we can assign 30 IPs (the network can support 30 hosts), we needed to subtract 2 from the network increment because there are two address that cannot be assigned to hosts, the broadcast address (.255) and the network address itself (.224).
- The first assignable IP is always one more than the network number, so the first valid IP address is 192.168.10.225 .
- The last assignable IP is always one less than the broadcast address, so the last valid IP address is 192.168.10.254 .
* Given 172.168.97.91/18. Find the network number, number of assignable IPs and host range using the table:
- /18 corresponds to 192 and indicates that VLSM is applied in the third octet of the subnetmask and the IP address. So the decimal subment mask is 255.255.192.0 .
- Find the network increment: 256-192=64, the network increment is 64 .
- Starting from 0 write all networks until passing the third octect (.97) of the given IP address (increments of 64): 0, 64, 128 ...
- We now know the
given IP is in between ...64 and 128... networks, we always choose the lowest one, in this case 64. That is the network number, 172.168.64.0!
(we write zeros in the octects to the right of the octect where VLSM is applied). - To find the number of assignable IPs when dealing with schemes where VLSM is not applied in the fourth octect (255.255.255.128 vs 255.255.128.0) binary is the way to go. Steps:
- We need the subnet mask in /X format, in this case /18 was given (use the table to convert X.X.X.X formatted subnet mask to /X format. Example: 255.255.248.0, we look for 248 in the table and since VLSM is applied in the third octect its corresponding equivalent is /21).
- IP addresses are 32 bit long. So, 32-18=14 ; Each etwork in this VLSM design are allocated 14 bits each.
- Finally, we find the number of usable IPs using the formula 2b-2; where b is the number of bits allocated to a network, we also need to subtract 2 because we cannot assign the broadcast and network addresses. 214 - 2 = 16382 ; We can have a total of 16,382 hosts in this network.
- The first assignable IP is always one more than the network number, so the first valid IP address is 172.168.64.1 .
- The broadcast address is one less than the next network. The network relating to this example is 172.168.64.0, the next network is 172.168.128.0 (because the network increment is 64); so, we subtract 1 from the third octect of the next network, 128-1=127. The broadcast address is 172.168.127.255 (we write 255s in the octects to the right of the octect where VLSM is applied).
- The last assignable IP is always one less than the last octect of the broadcast address. 172.168.127.254 .
* Given 10.29.45.6/21. Find the network number, number of assignable IPs and host range using the table:
- /21 corresponds to 248 and indicates that VLSM is applied in the third octet of the subnetmask and the IP address. So the decimal subment mask is 255.255.248.0 .
- Find the network increment: 256-248=8, the network increment is 8 .
- Starting from 0 write all networks until passing the third octect (.45) of the given IP address (increments of 8): 0, 8, 16, 24, 32, 40, 48...
- We now know the
given IP is in between ...40 and 48... networks, we always choose the lowest one, in this case 40. That is the network number, 10.29.40.0!
(we write zeros in the octects to the right of the octect where VLSM is applied). - To find the number of assignable IPs when dealing with schemes where VLSM is not applied in the fourth octect (255.255.255.128 vs 255.255.128.0) binary is the way to go. Steps:
- We need the subnet mask in /X format, in this case /21 was given (use the table to convert X.X.X.X formatted subnet mask to /X format. Example: 255.255.248.0, we look for 248 in the table and since VLSM is applied in the third octect its corresponding equivalent is /21).
- IP addresses are 32 bit long. So, 32-21=11 ; Each etwork in this VLSM design are allocated 11 bits each.
- Finally, we find the number of usable IPs using the formula 2b-2; where b is the number of bits allocated to a network, we also need to subtract 2 because we cannot assign the broadcast and network addresses. 211 - 2 = 2046 ; We can have a total of 2,046 hosts in this network.
- The first assignable IP is always one more than the network number, so the first valid IP address is 10.29.40.1 .
- The broadcast address is one less than the next network. The network relating to this example is 10.29.40.0, the next network is 10.29.48.0 (because the network increment is 8); so, we subtract 1 from the third octect of the next network, 48-1=47. The broadcast address is 10.29.47.255 (we write 255s in the octects to the right of the octect where VLSM is applied).
- The last assignable IP is always one less than the last octect of the broadcast address. 10.29.47.254 .
* Given 10.9.68.14/15. Find the network number, number of assignable IPs and host range using the table:
- /15 corresponds to 254 and indicates that VLSM is applied in the second octet of the subnetmask and the IP address. So the decimal subment mask is 255.254.0.0 .
- Find the network increment: 256-254=2, the network increment is 2 .
- Starting from 0 write all networks until passing the second octect (.9) of the given IP address (increments of 2): 0, 2, 4, 6, 8, 10...
- We now know the
given IP is in between ...8 and 10... networks, we always choose the lowest one, in this case 8. That is the network number, 10.8.0.0!
(we write zeros in the octects to the right of the octect where VLSM is applied). - To find the number of assignable IPs when dealing with schemes where VLSM is not applied in the fourth octect (255.255.255.128 vs 255.255.128.0) binary is the way to go. Steps:
- We need the subnet mask in /X format, in this case /15 was given (use the table to convert X.X.X.X formatted subnet mask to /X format. Example: 255.255.248.0, we look for 248 in the table and since VLSM is applied in the third octect its corresponding equivalent is /21).
- IP addresses are 32 bit long. So, 32-15=17 ; Each etwork in this VLSM design are allocated 17 bits each.
- Finally, we find the number of usable IPs using the formula 2b-2; where b is the number of bits allocated to a network, we also need to subtract 2 because we cannot assign the broadcast and network addresses. 217 - 2 = 131070 ; We can have a total of 131,070 hosts in this network.
- The first assignable IP is always one more than the network number, so the first valid IP address is 10.8.0.1 .
- The broadcast address is one less than the next network. The network relating to this example is 10.8.0.0, the next network is 10.10.0.0 (because the network increment is 2); so, we subtract 1 from the second octect of the next network, 10-1=9. The broadcast address is 10.9.255.255 (we write 255s in the octects to the right of the octect where VLSM is applied).
- The last assignable IP is always one less than the last octect of the broadcast address. 10.9.255.254 .
Remember the network range is from 172.168.64.0 to 172.168.127.255, but we do not use the first and last addresses.
* Cisco routers will reject configuration of networks that overlap with already configured networks in local interfaces.
* ip subnet zero
ACLs
* ACL ranges:
- Standard: 1-99, 1300-1999; Only inspect source IP address.
- Extended: 100-199, 2000-2699; Inspects source and destination IPs and ports.
* Standard ACL example:
R1(config)# access-list 15 permit host 10.1.1.2
R1(config)# access-list 15 deny host 10.3.1.20
R1(config)# access-list 15 permit 10.3.1.0 0.0.0.255
* Extended ACL example:
R1(config)# access-list 100 permit tcp any host 172.16.25.10 eq 80
R1(config)# access-list 100 deny host 10.15.25.5 host 172.16.25.15
R1(config)# access-list 100 permit ip 10.15.25.0 0.0.0.255 host 172.16.25.15
* Apply an access list to an interface:
R1(config-if)# ip access-group 100 [in|out]
* The first match determines whether the Cisco IOS software accepts or rejects the packet. Because the Cisco IOS software stops testing conditions after the first match, the order of the conditions is critical. If no conditions match, the router rejects the packet because of an implicit deny all clause at the end.* Specify more specific rules first, deny or allow TCP/UDP/ICMP rules first.
* IP Named ACLs.- Allow the deletion of a single statement in the list, allows naming of the list; Can be standard or extended.
* IP Named ACLs examples:
- Standard:
R1(config)# ip access-list standard "MyACL_name" R1(config-std-nacl)# deny host 10.3.1.20 R1(config-std-nacl)# permit 10.3.1.0 0.0.0.255
- Extended:
R1(config)# ip access-list extended "MyACL_name" R1(config-ext-nacl)# permit tcp host 10.3.1.20 host 172.16.25.10 eq 80 R1(config-ext-nacl)# deny tcp any host 172.16.25.10 eq 80 R1(config-ext-nacl)# permit ip any any
* Dynamic ACLs (Lock & Key).- The router asks for a username and password; after successfully authenticating the user, the router dynamically changes its ACL to permit traffic from the IP address of the host that just sent the authentication packet. After a period of time, the router removes the dynamic entry in the ACL.
* Reflexive ACLs.- An enterprise user must first initiate a new session, then the router records the source and destination IPs and ports, as a result the reflexive ACL will only allow packets whose addresses and ports matches the original packet.
* Time Based ACLs.-
IP Routing
* IP, TCP and UDP headers:

* Common protocols that use TCP/UDP:
| UDP | TCP |
|---|---|
| DHCP, ports 67 and 68 | FTP,port 21 |
| DNS, port 53 (primarily UDP) | DNS, port 53 (optionally TCP) |
| SNMP, port 161 | HTTP, port 80 |
| TFTP, port 69 | HTTPS, port 443 |
| POP3, port 110 | |
| SMTP, port 25 | |
| SSH, port 22 |
* Flow control mechanisms provide receiving hosts a way to control the transmission speed. Flow control mechanisms include : congestion avoidance, windowing, buffering.
* Classful and Classless routing dictate how a default route is used:
- Classful Routing.- The router first matches the class A, B or C network in which the destination resides, if a class A, B or C network is found, the router then looks for the specific subnet number; If the specific subnet is not found the packet is discarded. In this case the default route is not used.
In a nutshell, when a specific subnet is not found in the routing table, ONLY use the default route if no other network/subnet of the same class is found in the routing table.
- Classless Routing.- When a specific subnet is not found in the routing table, use the default route.
* Autosumarization and manual sumarization
- Auto-Summarization.- Causes problems on discontigious networks. RIP and EIGRP defaults to auto-summarization, OSPF do not supports it. <--check plz
- Manual-Summarization.-
* PING
* Extended PING features:
- Able to specify timeout value
- Able to specify datagram size
* TRECEROUTE
* TTL expired in transit: routing loop
* IP routing protocols (Interior Routing Protocols):
- Classfull protocols:
- RIPv1:
- No authentication
- Only support auto-summarization
- Sends updates as broadcasts (255.255.255.255)
- -
- Administrative distance is 120
- IGRP
- Administrative distance is 100
- RIPv1:
- Classless protocols:
- RIPv2
- Supports authentication
- Supports manual summarization
- Sends updates as multicast (224.0.0.9)
- -
- Sends periodic updates every 30 seconds
- Administrative distance is 120
- Route metric is hop count
- OSPF
- -----
- Hello packets are sent to multicast 224.0.0.5
- Hellos are send by default every 10 seconds for an Ethernet link and 30 seconds for a non broadcast link
- Designated routers use multicast 224.0.0.6 for routing updates
- Designated routers are elected in broadcast and non-broadcast multiaccess networks
- Sends event triggered updates
- Administrative distance is 110
- EIGRP
- RIPv2
- BGP.- Routes between Autonomous Systems; BGP V4 adds support for classless routing.
* Use the nework command to turn routing interfaces
RIP
Timers (in seconds)
Update: 30
Invalid: 180
Hold Down: 180
Flush: 240
OSPF
* Router ID selection proccess
- Manually configured. R1(config-router)# router-id "ip" .
- If not manually set, the loopback with the highest IP and up/up status becomes the router id.
- Lastly, if not manually set and no loopback interfaces exist, the highest IP among all up/up interfaces becomes the router id.
• The router sending the Hello with the highest OSPF priority setting becomes the DR.
• If two or more routers tie with the highest OSPF priority setting, the router sending the Hello with the highest RID wins.
• It's not always the case, but typically the router with the second-highest OSPF priority becomes the BDR.
• An OSPF priority setting of 0 means that the router does not participate in the election and can never become the DR or BDR.
• The range of OSPF priority values that allow a router to be a candidate are 1 through 255.
• If a new, better candidate comes along after the DR and BDR have been elected, the new candidate does not preempt the existing DR and BDR.
EIGRP
* Differentiates between internal and external routes.
* Uses a 32-bit metric.
WANs
* HDLC
* PPP link username and password
//Local router
router(config)# hostname "R1"
R1(config)# username "R2" password "MyPass"
R1(config-if)# ppp authentication chap
R1(config-if)# encapsulation ppp
//Remote router
router(config)# hostname "R2"
R2(config)# username "R1" password "MyPass"
R2(config-if)# ppp authentication chap
R2(config-if)# encapsulation ppp
* CHAP authentication whit PAP as the fallback method on a serial interface: (config-if)# ppp authentication chap pap
* Frame-Relay PVC encapsulations:
- Cisco (default)
- IETF
* Frame Relay LMI types:
- Cisco (default)
- ANSI
- Q.933A
NAT
* Static NAT configuration:
- Configure the translation
R1(config)# ip nat inside source static 192.168.1.5 69.1.1.5
- Specify inside interface (ethernet)
R1(config-if)# ip nat inside
- Specify outside interface (serial)
R1(config-if)# ip nat outside
- Identify inside addresses to be translated
R1(config)# access-list "ACL_number" permit 192.168.1.0 0.0.0.31
- Specify the public addresses to be used for translation
R1(config)# ip nat pool "MyPool" 69.1.1.1 69.1.1.31 netmask 255.255.255.224
- Configure the translation
R1(config)# ip nat inside source list "ACL_number" pool "MyPool"
- Specify inside interface (ethernet)
R1(config-if)# ip nat inside
- Specify outside interface (serial)
R1(config-if)# ip nat outside
- Identify inside addresses to be translated
R1(config)# access-list "ACL_number" permit 192.168.1.0 0.0.0.255
- Configure the translation
R1(config)# ip nat inside source list "ACL_number" interface S0/0 overload
- Specify inside interface (ethernet)
R1(config-if)# ip nat inside
- Specify outside interface (serial)
R1(config-if)# ip nat outside
- Configure the translations
R1(config)# ip nat inside source static tcp 172.168.13.50 80 199.198.5.1 80 extendable R1(config)# ip nat inside source static tcp 172.168.13.14 25 199.198.5.1 25 extendable
- Specify inside interface (ethernet)
R1(config-if)# ip nat inside
- Specify outside interface (serial)
R1(config-if)# ip nat outside
- Inside Local.- A private/public IP address assigned to a host in the inside network (LAN).
- Inside Global.- The IP address of an inisde host as it appears to the outside network (typically the Internet).
- Outside Local.- A private/public IP address of a host in the outside network as it appears to the inside network.
- Outside Global.- The configured IP address of a host in the outside network.
* IPsec.- Open standard framework that is commonly used in VPNs to provide secure end-to-end connections
* Data Integrity.- Ensures that data is unaltered between the sender and the recipient.
* Data integrity algorithms: HMAC-MD5 and HMAC-SHA-1
* Authentication.- Ensures that data can be read only by its intented recipent.
* ESP.- Provides confidentiality.
IPv6
* EUI-64 address format
* Multicast address for all routers in the same network segment: FF02::2
Debug Commands
* debug PPP authentication
* debug IP icmp
* debug IP eigrp